PCI Failure
Today we received notification during a PCI compliance check that our Microsoft CRM 2011 server was not PCI Compliant.

The cause of the lack of compliance was due to the server accepting connections via an SSL v 2.0 protocol.
Synopsis : The remote service encrypts traffic using a protocol with known
weaknesses . Description : The remote service accepts connections encrypted
using S S L 2.0, which reportedly suffers from several cryptographic flaws and has
been deprecated for several years . An attacker may be able to exploit these
issues to conduct man-in-the-middle attacks or decrypt communications between
the affected service and clients . See also : http://www.schneier.com/p
aper-ssl.pdf
Solution: Consult the application’s documentation to dis able S S L 2.0 and us e
S S L 3.0 or TLS 1.0 instead. Risk Factor: Medium / CVS S Bas e S core : 2
(AV:R/AC:L/Au:NR/C:P/A:N/I:N/B:N)
Perhaps not the worlds biggest deal, as the SSL certificates in place are using the SSL 3.0 however we needed to remove the V2.0 for compliance with PCI.
The solution turned out to be no so easy… Mostly due to the fact that we are using a 64bit Windows 2008 server and Microsoft have only appeared to provide details on fixing 32 bit servers to remove SSL v2.
We did manage to get there and this is what we had to do
Remove SSL v2
You need to run the following commands at a command prompt on the server:
REG ADD “HKLM\System\CurrentControlSet\Control\SecurityProviders\SChannel\Protocols\SSL 2.0\Server” /v Enabled /t REG_DWORD /d 0 /f
REG ADD “HKLM\System\CurrentControlSet\Control\SecurityProviders\SChannel\Protocols\SSL 2.0\Client” /v Enabled /t REG_DWORD /d 0 /f
REG ADD “HKLM\System\CurrentControlSet\Control\SecurityProviders\SChannel\Protocols\SSL 3.0\Server” /v Enabled /t REG_DWORD /d 1 /f
REG ADD “HKLM\System\CurrentControlSet\Control\SecurityProviders\SChannel\Protocols\SSL 3.0\Client” /v Enabled /t REG_DWORD /d 1 /f
REG ADD “HKLM\System\CurrentControlSet\Control\SecurityProviders\SChannel\Protocols\TLS 1.0\Server” /v Enabled /t REG_DWORD /d 1 /f
REG ADD “HKLM\System\CurrentControlSet\Control\SecurityProviders\SChannel\Protocols\TLS 1.0\Client” /v Enabled /t REG_DWORD /d 1 /f
We created a batch file to make this easier.
You can download the file here, and extract the batch file. Then double click the file called: “DisableSSLv264bit.bat”.
Then Reboot the server.
All it will do is run the above commands and in the registry it will add:
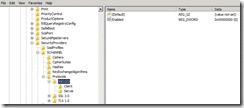
and similar sets to enable SSL v3 and disable SSL v2.
Then you can use a free test service here:
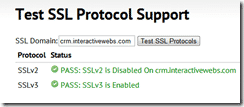
to check that you are disabled.
A failure like this: http://foundeo.com/products/iis-weak-ssl-ciphers/test.cfm

indicates something did not take correctly.
If you are using a 32 bit version of windows. (Not possible with CRM 2011) but possible otherwise, then you can use the Microsoft tool here: http://support.microsoft.com/kb/187498/en-us
Hi,
i did everything you said , but my server still response that SSLV2 is enable.
what can be happening?
SSLv2 [Enabled] FAIL: SSLv2 is Enabled on [my site here] You Must Disable It SSLv2 is weak and should be disabled.
thanks
Hi again,
i found my fault…
when i typed the DWORD key i wrote the name “ENABLE” and don’t “ENABLED” as you posted
sorry, it is working now
Glad you sorted it.
hi
I tried same quary wit h power shell . it showing
SSLv2 PASS: SSLv2 is Disabled On eisapp-prep SSLv2 is weak and should be disabled. More information.
SSLv3 SSLv3 is Disabled SSLv3 should be enabled.
Same issue as above by kirtiagre. I Can’t get SSLv3 to work even it’s enabled in the registry.
Pingback: My Homepage